 Image by AI.
Image by AI.
Andrew Paquette, Ph.D., has discovered a never-before-seen algorithm in the Wisconsin Election Commission’s (WEC) voter registration database, leaving no doubt someone has penetrated the WEC’s computer system to impose a criminal reordering on the voter files. This finding alone should draw the attention of Director of National Intelligence Tulsi Gabbard, Attorney General Pam Bondi, and FBI Director Kash Patel. Yet, to date, we see no action whatsoever from the DOJ or the FBI investigating criminal election fraud.
Paquette first observed that the WEC voter roll had an unusually high number of voter records that ended in zero. Assuming that the WEC voter roll assigned voter ID numbers sequentially, without breaks or outside manipulation, records ending in 0, 1, 2, 3, 4, 5, 6, 7, 8, and 9 should appear with equal distribution. As seen in Table 1, voter records ending in zero occurred in 30.6 percent of the voter records, while those ending in numbers 1 through 9 ended with each number appearing equally at 7.7 percent of the time.
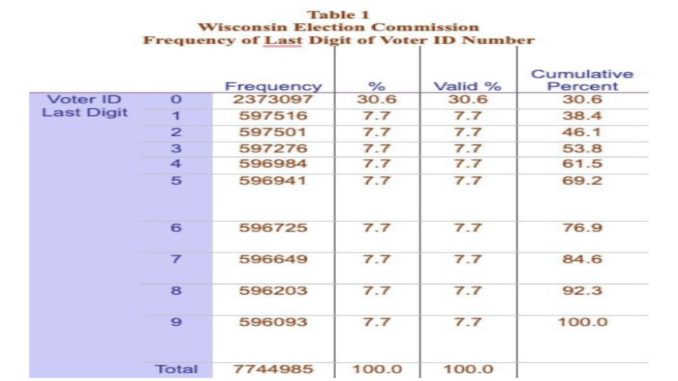
Paquette was at a loss to explain this irregularity until he realized that every voter ID record ending in zero had two different Wisconsin voters assigned the same voter ID number. In searching the database, Paquette confirmed that in every case where the same voter ID number was assigned to two different voters, the voter record ended in zero.
We have labeled the two voter IDs tied to WEC voter records ending in zero as “doubles,” a term devised to distinguish this phenomenon from the “modified duplicates” that Paquette previously found in the WEC voter database. “Modified duplicates” involve making multiple voter records for the same voter, which can be done, for instance, by assigning a different birthdate or address to each duplicated record. Because duplicated voters each have different dates of birth or other addresses, the “modified duplicates” appear to be different people.
The point of the “modified duplicate” scheme is to create false voters, all of whom nevertheless get legitimate state voter ID numbers. The non-existent “multiple duplicate” voters can then be hidden back in the voter roll, identifiable to the criminals by “algorithm locator numbers,” so they are available for use in fraudulent mail-in ballot schemes.
Why the “doubles” scheme assigns the same voter ID number to two different voters is more difficult to figure out. What is also not clear is whether one or both of the “doubles” are real voters or if both of the “doubles” voters could be fictitious.
A scheme this complicated must operate through a computer algorithm that creates “doubles” for every voter ID record ending in zero in a WEC database of over 7 million voters. That is, whatever rule is applied to pick the two voters who constitute the “doubles” in a database with over 7 million voters needs an algorithm if the scheme is to be applied, monitored, and updated on an ongoing basis.
Put another way, this cannot be random. Because there’s numerical consistency when it comes to all zero-ending records involving doubles and all duplicate voters having only zero-ending voter IDs, that implies a set of programming instructions (i.e., an algorithm) telling the system to create these records in formulaic fashion.
The probability that a scheme this complicated, consistent, and massive could happen by chance is near zero. The only logical conclusion is that someone penetrated the WEC server to embed the rule that would consistently alter the entire WEC voter registration database.
The WEC “doubles” scheme violates the Help America Vote Act (HAVA, 2002), which requires that each voter have a unique voter ID number and that no coded information not readily perceptible to election workers may be embedded secretly in the state voter roll database. Given the HAVA mandate that each registered voter must have a unique voter ID number, there is no administrative necessity justifying the fact that, as it now stands, every record in the WEC voter database with a voter numbering ending in zero is associated with two distinct voters.
We have previously argued that President Trump has chosen to elevate the election fraud investigation into a national security matter by bypassing a DOJ criminal investigation with Director of National Intelligence Tulsi Gabbard at the helm. The Department of Homeland Security has exercised authority in Arizona to review Arizona’s state voter roll to verify the citizenship of voters under the authority of President Trump’s Executive Order.
On April 23, 2025, Tulsi Gabbard referred two members of the intelligence community for criminal prosecution by the DOJ for leaking classified information to the Washington Post and the New York Times. This was information about the U.S. military strike on Houthi rebels. The leak was intended to harm Secretary of Defense Pete Hegseth. Gabbard indicated that her action would “serve as a warning” to those “deep-state criminals” who “for partisan political purposes” sought “to undermine President Trump’s agenda.”
In that spirit, and in the absence of aggressive DOJ/FBI efforts to investigate deep-state criminals, Gabbard may have found a methodology that has a chance of spurring Bondi and Patel to action.
We now have abundant evidence that the WEC maintains a criminally infected voter registration database that was used in the 2024 general election and in the recent 2025 election for a seat on the Wisconsin State Supreme Court. Bondi needs to appoint a DOJ election integrity Task Force that will give Patel’s FBI sufficient subpoena power to seize WEC computers, voter registration files, and relevant internal documents, including emails. What’s holding Bondi and Patel back?
GodsFiveStones.com is a tax-deductible 501(c)3 foundation created by Jerome R. Corsi, Ph.D., and Karladine Graves, M.D., managed by Capstone Legacy Foundation. As reported on GodsFiveStones.com, Andrew Paquette, Ph.D., has discovered cryptographic algorithms in the State Board of Elections voter registration databases in New York, Ohio, Pennsylvania, Georgia, Arizona, Florida, New Jersey, and Oklahoma.



One day voting ONLY
One valid ID (no fake driving lic.)
Proof of citizenship
One paper ballot
No electronic
Hand counting
Results within 24hrs of closure of boots
No mail-in
No drop box
Clean voter rolls
No lawyers
Term limit
Etc…
I am pretty certain that even though the Trump Administration strives for transparency, ongoing criminal investigations are not made public so as not to inform the criminals that they are being investigated until it is time to inform them. So just because we have no evidence that the investigation is happening, absence of evidence is not evidence of absence.
There are a finite number of individuals who have legitimate permission to access a state’s election commission servers, and a finite number of individuals from DHS who might have permission to access to the servers. In addition, there are an indeterminate number of individuals either inside the US or outside the US that have the ability and criminal intent to hack into these servers.
It is helpful to have found an algorithm that can account for this particular type of WEC ballot fraud. But there are so many different types of ballot fraud that the options are nearly infinite, including the method shown in Georgia that the election database can be changed with a method as crude as a ball point pen inserted into an electronic voting machine.
Americans are not going to ever feel secure with our electoral system until we go back to paper ballots, Voter ID, same day voting, and same day tabulation of results. Electronic voting machines are as secure as sieves, vulnerable to attack and changing of the ballots at multiple points in the electronic database, and hackable at a distance due to their internet connectivity.
If I read the numbers correctly, 9 * 7.7% = ~70% of all the voter identification numbers currently assessed to be valid. This leaves ~30% which cannot be correctly associated with valid voters. Taking the 7.7% from the 1-9 range means that we could assume that a quarter of the numbers ending in 0 might be valid which means that 3 of every four of the in 0 ending numbers rather than only one must be considered invalid.
There are more problems hidden in the distribution of voter IDs than currently indicated. For example, does the number of voter IDs agree with the number of valid voters? Does the distribution of these seemingly fake voter IDs spread out evenly across all the voting centers (indicating a real intention of fraud) or are there groups of voter IDs in the sames counties?
My guess is that an concentrated examination of all voter IDs will turn up more probable issues.
The final questions are, does this scheme turn up in other states? why is there no concentrated effort by Bondi and Patel to get to the source of this problem? is there perhaps more going on behind the scene than has been exposed here?
At any rate, any legal US citizen should now become aware of the fact that the investigation initiated by DJT must be completed as quickly as possible to ensure that the next voting season is correctly accounted.